

The system implementation involves a number of distinct yet inter-related functions. The following dataflow diagrams show the interaction flows in the system. The last dataflow case: “Manage User Account” is slated for Phases 2 and 3 of the project.
The top-level dataflow diagram lists the interactions between the system. This interaction is further exploded for each dataflow in the subsequent diagrams:
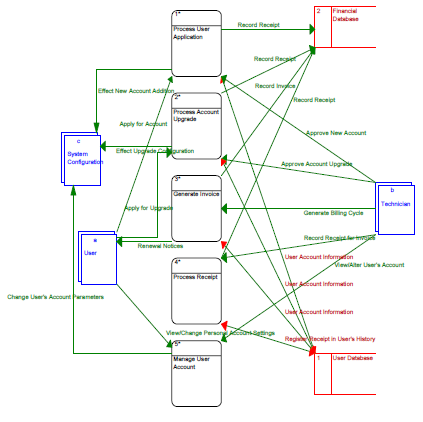
The Manage User Account Data Flow is slated for implementation in phases 2 and 3 of the project.
The dataflow will be managed using a combination of HTML pages, Javascript functions within HTML, CGI scripts, embedded PERL within HTML, and some shell script and PERL script library functions.
To visualize the data flow as it relates to the actual structure of the web site, the following Web Navigation Flow Diagrams were prepared. Figure 2 shows the pages available through the public web space to all users and potential users. Note that while an initial applicant can make an application without any sort of authentication, a user requesting an upgrade and all other user functions require the user to be authenticated prior to performing any of these actions.
The volunteer portion of the web site will be secured using the inherent access controls of the Apache web server. As such, no user authentication library calls are required, the processing flow is somewhat simplified.
Links
[1] https://niedermayer.ca/user/login?destination=node/79%23comment-form
[2] https://niedermayer.ca/user/login?destination=node/80%23comment-form
[3] https://niedermayer.ca/user/login?destination=node/81%23comment-form
[4] https://niedermayer.ca/user/login?destination=node/82%23comment-form
[5] https://niedermayer.ca/user/login?destination=node/83%23comment-form
[6] https://niedermayer.ca/sites/default/files/large_dfd4.PNG
[7] https://niedermayer.ca/user/login?destination=node/84%23comment-form
[8] https://niedermayer.ca/user/login?destination=node/85%23comment-form
[9] https://niedermayer.ca/user/login?destination=node/86%23comment-form